28.05.2020
WordPress Hacks
Security breach in WordPress – database upgrade without an admin session
READING TIME: MIN
Table of Content
Hello WordPress folks,
Recently I experienced an interesting breach in WordPress security, which I haven’t found discussed anywhere yet (excuse me if so!).
It seems WordPress allows any single visitor to perform a database upgrade after a core system upgrade.
How is this possible?
In order to notice this your WordPress installation had to be updated recently with a version jump that requires database upgrade as well. This can happen even by itself because the majority of WordPress installations are upgrading by themselves using the wp-cron.
So let’s say your WordPress has been recently updated from v 4.9 to 5.4. Then the upgrade is usually finished with this screen, asking you to upgrade the database.
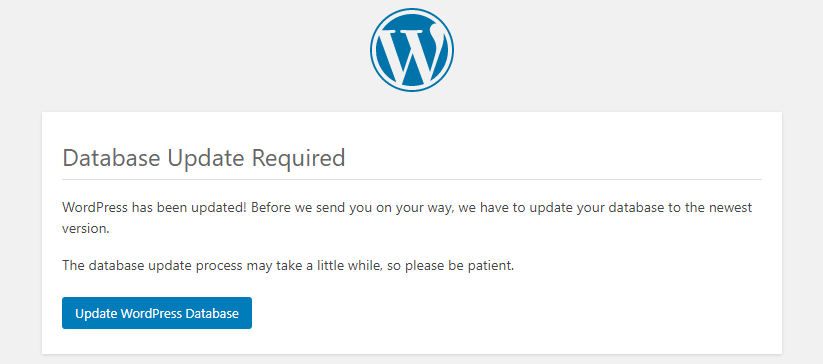
This seems pretty normal and straight forward. Yes, for sure if you are a logged-in the administrator that just performed the upgrade.
The problem – you don’t have to be logged to perform this
However, if you decide to destroy your session and open the /wp-admin as a guest visitor – you will notice the same screen. We attach it with a screenshot of our active cookies. No logged-in session is present as you can see.
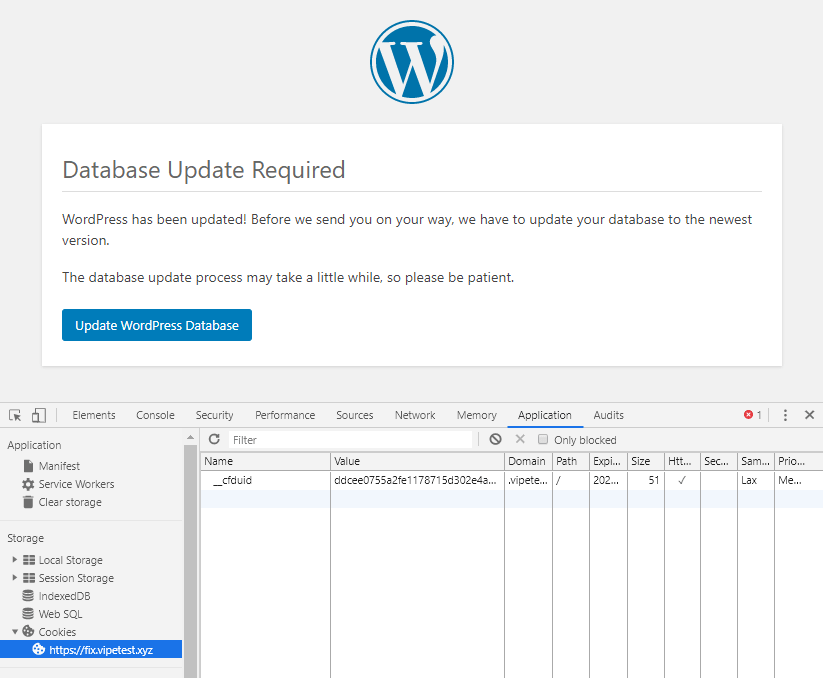
That doesn’t seem so right. Let’s watch the whole process with the cookies tab opened in our specially recorded for the case YouTube video.
As you can see we first performed the database upgrade as a guest visitor and after that, we logged ourselves in the admin area.
What are the security breaches?
For some of you, this may sound like not such a big deal, but actually, there are a couple of problematic points here:
- Database upgrade has the potential to break the whole database if it met some conditions;
- It gives a guest visitor a privilege to perform an action that a visitor must not be able to;
- It exposes the fact the website has been recently upgraded and no one has logged since then;
How can we prevent this?
It seems the chance a guest visitor to face this is if the visitor intentionally tries to visit your /wp-admin or /wp-login.php sections. That means a simple admin URL change should do the trick. You can do this with almost any security plugin. Of course, if you need advanced security measures taken on your website, you can always take a look at our anti-hack service.
More on The Topic
- Automation and Tooling in WordPress Operations
- WordPress as Organizational Memory
- WordPress Performance as a Leadership Responsibility
- The Future of Leadership in Hybrid Workplaces
- Block Editor Patterns That Control Your Team
The content of this website is copyrighted and protected by Creative Commons 4.0.



